-
Hacking : A Beginner's Guide to Learn and Master Ethical Hacking with Practical Examples to Computer, Hacking, Wireless Network, Cybersecurity and Penetration Test (Kali Linux)
This Book Includes :Hacking With Kali Linux : A Comprehensive, Step-By-Step Beginner's Guide to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingHacking: A Comprehensive, Step-By-Step Guide to Techniques and Strategies to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestAre you fascinated by the idea of Hacking?Do you want to learn the secrets of ethical hackers?This complete , step by step guide will teach you everything that you need to know!In this b... [Read More]
- ASIN: B07RY3TBBW
- ASIN: B07RY3TBBW
-
JavaScript: Best Practices to Programming Code with JavaScript - eBook
Learn how to write effective and efficient JavaScript code for programming success and continue your progress towards JavaScript programming mastery!In this Definitive JavaScript Guide on Best Practices, you're about to discover how to...Code more efficiently
- UPC: 760976654
-
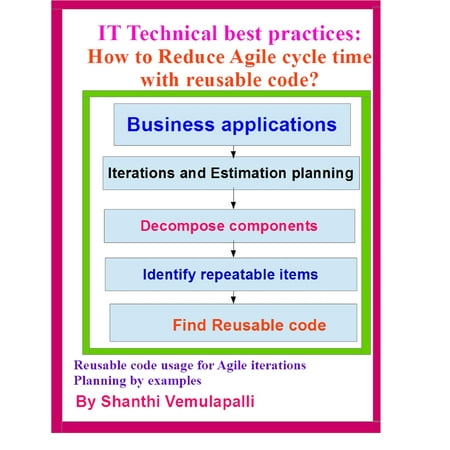
IT Technical best practices: How to Reduce Agile cycle time with reusable code? - eBook
In many Agile transformation sessions the Agile practitioners or savvy’s discuss more on the process related activities rather than elaborating on the technical or software engineering process steps to reduce the cycle time. At the
- UPC: 225671033
-
Heroic Leadership : Best Practices from a 450-Year-Old Company That Changed the World
Shows how Jesuits have successfully grappled with the same challenges that test great companies today with an emphasis on their adopted values: self-awareness, ingenuity, love, and heroism.
- UPC: 3378981
- Rating: 4.5

-
Guidance for It Asset Management (Itam) : Step by Step Implementation Guide with Workflows, Metrics, Best Practices and Checklists
Guidance for ITAM provides a direction in a concise, clear, user friendly and understandable way for all the ITAM audiences (newbie's, intermediates, experts). This book is not just for ITAM process consultants or management folks
- UPC: 53408889
-
Effective Cybersecurity : A Guide to Using Best Practices and Standards
The Practical, Comprehensive Guide to Applying Cybersecurity Best Practices and Standards in Real Environments In Effective Cybersecurity, William Stallings introduces the technology, operational procedures, and management practices needed for successful cybersecurity. Stallings makes extensive use
- UPC: 56133768
-
Web Content Management : Systems, Features, and Best Practices
"Looking to select a web content management system (CMS), but confused about the promises, terminology, and buzzwords? Do you want to understand content management without having to dive into the underlying programming? This book provides
- UPC: 44979023
-
AWS System Administration : Best Practices for Sysadmins in the Amazon Cloud
With platforms designed for rapid adaptation and failure recovery such as Amazon Web Services, cloud computing is more like programming than traditional system administration. Tools for automatic scaling and instance replacement allow even small DevOps
- UPC: 40401572
-
Defensive Security Handbook : Best Practices for Securing Infrastructure
Despite the increase of high-profile hacks, record-breaking data leaks, and ransomware attacks, many organizations don't have the budget to establish or outsource an information security (InfoSec) program, forcing them to learn on the job. For
- UPC: 55479617
Understanding Logs & Log Management in RHEL 7
Python Tutorial: Logging Basics - Logging to Files, Setting Levels, and Formatting
BIND 9 logging best practices
© 10Toply.com - all rights reserved - Sitemap 10Toply.com is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for sites to earn advertising fees by advertising and linking to Amazon.com